The majority of companies employ applications made up of several elements, some of which are acquired through open-source libraries, others from suppliers, and still others that are built and changed by programmers. Each source has its own set of constraints.
For example, OSS and third-party software licencing may change over time or include use limits. A typical SBOM system survey identifies and describes these coding components.
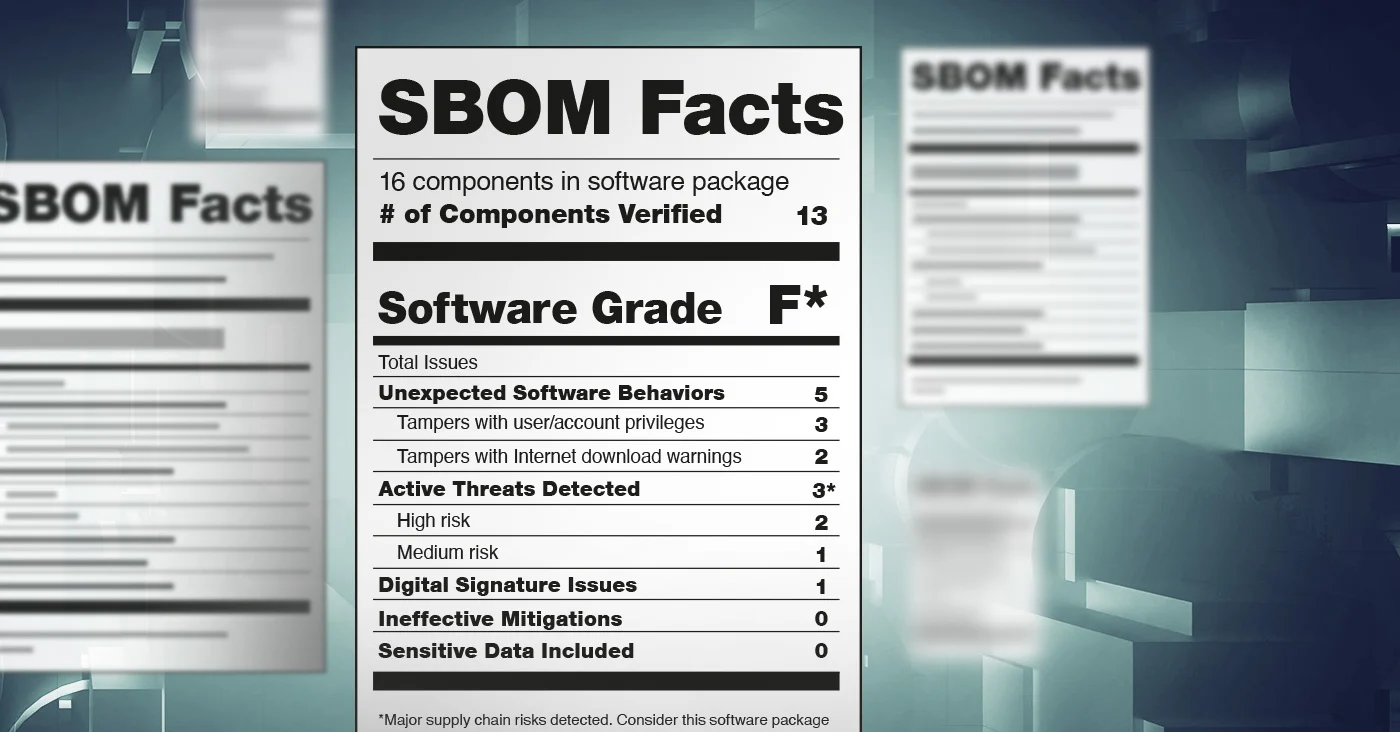
Organizations that struggle to recognise the flaws in their code expose themselves to financial and security risk. By creating a software bill of materials sbom for cyber security programme, and a corporation may get the following benefits:
Vulnerability detection and repair SBOM systems inventory code subcomponents, allowing researchers to uncover code with known security problems. When a significant defect is reported, security professionals check SBOM artefacts to determine whether the code is impacted.
This allows incident response personnel to identify weaknesses and prioritise mitigation steps. Furthermore, it enables executives to respond quickly and confidently when communicating with the board, clients, investors, and regulators.
Management of software licences SBOM solutions make it simpler to handle OSS and third-party software licences, which may be difficult and develop over time.
inally, by ensuring developers are consistently able to identify the approved use cases for OSS and third-party software, this saves firms from financial risk associated with incorrect or unlawful use of third-party software. It also helps compliance teams react to audits or licencing claims.
Optimization of the software development life cycle (SDLC). SBOM efforts may help a company’s SDLC. Problems such as known vulnerabilities or licencing issues may be discovered during the SDLC by creating an SBOM at predefined intervals.
Early problem-solving by teams reduces costs and delays. Businesses can build, deploy, and run software more rapidly and effectively thanks to SBOM efforts.
As they build the code, developers, for example, create an initial SBOM that identifies the dependencies existing in the application. During testing and packaging, vulnerabilities and additional dependencies are discovered, and the SBOM is updated when the code is used.
When vulnerabilities are discovered during operations, the SBOM programme will alert developers that a repair is required. When you patch, the SBOM is updated once again.
The stages to building an SBOM programme are to invest, produce, integrate, and design.
Understanding the benefits and challenges of OSS development, it is clear that SBOM programmes are critical to safer code and a robust company.
Firms may achieve this goal by focusing on four critical practises when adopting SBOM programmes:
Invest in SBOM capabilities by building on existing software composition analysis (SCA) tools. Many organisations have SCA capabilities. Depending on how strong the capabilities are, teams may use this as a foundation for developing an SBOM application.
Leadership may make better use of resources by deciding which SBOM tools can be purchased rather than developed in-house. Product managers should collaborate with a reputable vendor to develop software that easily and automatically interacts with a continuous integration and continuous deployment (CI/CD) pipeline.
The capacity to automate SBOM may be developed in-house or obtained from a third-party source.
Create an SBOM programme in collaboration with a cross-functional team. The SBOM programmes are divided into numerous organisational divisions, each with a distinct purpose to accomplish. It is critical to build an SBOM programme with a cross-functional team.
Because SBOM initiatives influence all parts of the company, this team should include people from several disciplines, such as developers, information security, procurement, legal, risk, privacy, and compliance.
Each participating team should be represented at decision-making levels, and their requests should be taken into account at all times.
SDLC should include SBOM. SBOM tools benefit developers by detecting defects and licencing issues early in the development process. Organizations that analyse their development processes and integrate SBOM generation and evaluation at different points of the development life cycle receive the greatest results.
The development of automated SBOM production and review capabilities reduces developer work and encourages them to experiment with novel techniques of operation.
Design of SBOM governance. Extra structure, as well as cross-functional collaboration and communication, may be required to enhance acceptance, compliance, and cooperation in SBOM projects. It may be difficult to persuade developers to follow SBOM rules in organisations with a decentralised or nonhierarchical culture.
The security benefits and SDLC efficiency enable increased developer buy-in. Organizations may also consider a governance framework that specifies roles and responsibilities for SBOM-related activities.