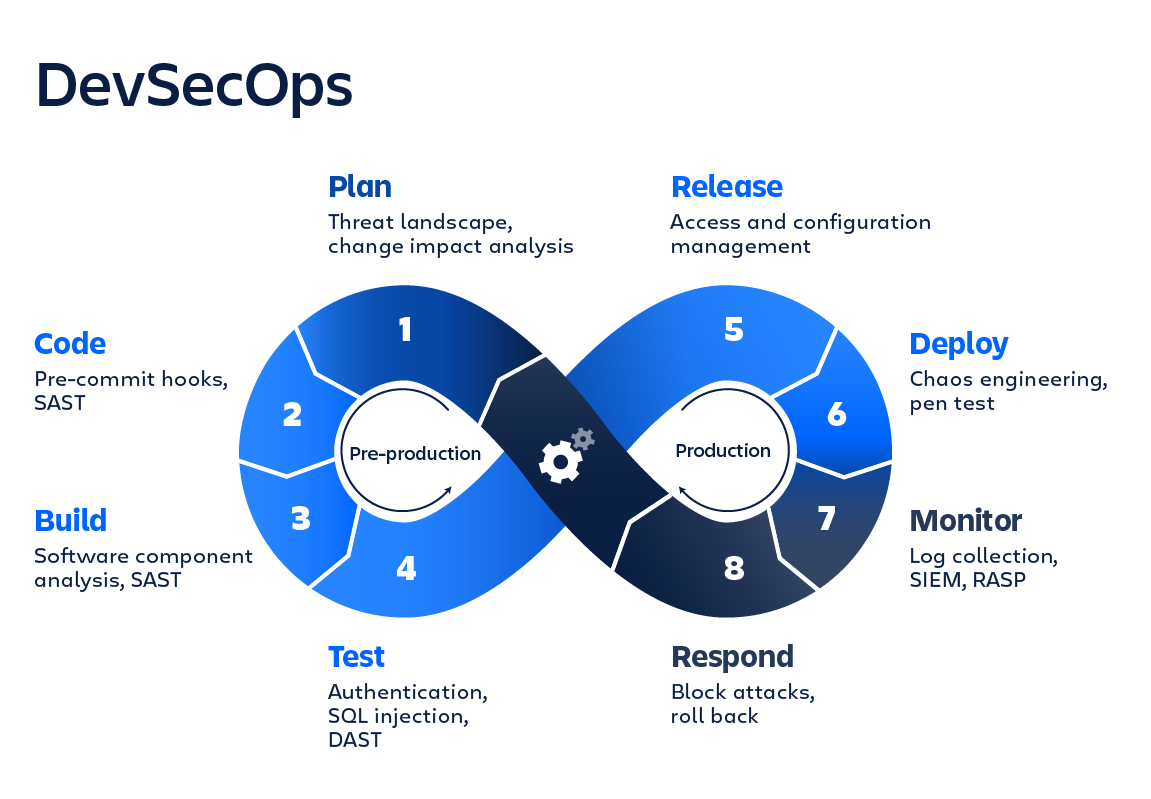
Introduction
Over the last few years, DevOps has provided IT companies with a highly cooperative approach and rapid product distribution. DevOps has become the preferred technology solution for so many IT firms because of its adaptability and capabilities to demonstrate short release cycles.
According to a DevOps Trend report, nearly all businesses revealed positive changes after implementing DevOps practices.
However, because of the increasing digital presence and advancing tech, the IT security problem is something we shouldn’t ignore!
The truth is that DevOps is also not completely secure from the risks of the Digital Age. With the number of internet dangers increasing all the time, arising a strong need for DevOps security.
But, don’t worry!
In this blog, we will discuss what the team “DevOps security” means and some of the best practices to achieve it.
What is the term “DevOps Security”?
The term “DevOps security” refers to an ideology that integrates the words “advancement,” “processes,” and “safety.” The goal is to break down any obstacles between software development and IT operations.
According to Verizon research, nearly 58 percent of companies were victims of a data breach last year, with 41 percent caused by software bugs. Companies can lose a lot of money and even their reputation in the market because of such breaches. (Add this para in the different box-like structure)
It aims to protect the entire DevOps environment with sophisticated techniques, regulations, procedures, and new tech.
DevOps security is commonly referred to as DevSecOps, and it seeks to enhance security by improving coordination and mutual accountability across the entire DevOps work process.
Why is it crucial to implement DevOps Security?
DevOps eliminates silos and adds a new degree of effectiveness to the software development process, but it is hard to execute and can create problems when first implemented.
For example, because development and information technology are two different departments – that work relatively independently, the spontaneous incorporation of the two can cause disruptions.
The revelation of an event, such as a security flaw, often uncovers DevOps failure.
In this case, a secure DevOps landscape uses various tools, procedures, and regulations to allow quick and safe releases. With DevOps, we can implement the most stringent security measures throughout the application development process.
Check out the best DevOps practices to ensure more protection!
1. Adopting the best coding standards
Developers primarily focus on creating the application’s features and neglect to include the security features; as a result, they fall short in terms of security.
However, with today’s rising cyber threats, you must ensure that your development team knows the best security practices when developing the application.
They should be familiar with the security tools that can assist them in identifying the security flaws in their code as they are being written so that they can quickly adjust the code and fix the threats and risks, which will minimize complications later on!
2. Using the PAM (privileged access management)
The DevOps team members offer unregulated access to multiple individuals about privileged accounts, such as root, admin, etc. These individuals frequently share credentials, removing the likelihood of a smooth audit trail.
Orchestration, configuration management, and other DevOps techniques may be given extensive privileges as well. And greater privileged access increases the threat surface.
Imposing the least privileged access reduces opportunities for internal or external hackers to ramp up privileged user rights or manipulate software flaws.
To protect the future of software development, organization privileged access management (PAM) workarounds can digitize the control, tracking, and inspection of special access, and also the full implementation of secrets/privileged credential monitoring.
3. Make the proper use of DevOps secret management.
DevOps teams employ various tools to digitize software procurement, system integration, and application deployment.
However, all of these require hidden planning because developers save privileged account info, secure shell (SSH) keys, application programming interface (API) tokens, as well as other needed tools, even in the manufacturing environment.
DevOps is good, but DevSecOps is better!
Says Gartner! (Add this as a quote)
This is evidently an attack method, providing cyber criminals with a means to steal business resources and interrupt the entire network.
With DevOps secret management, extracting or hiding these embedded login details from code is crucial to protect the software from potential risks.
4. Proper optimizations by analyzing & managing metrics
Monitoring and controlling the right performance measures guarantees that your DevOps lifecycle runs smoothly.
You can maintain your funnel active and steady by effectively measuring performance measures like lead time, recognition time, construct finishing time, and issue intensity. You can implement an alert method for prompt detection and prevention of any process difficulties.
You can optimize DevOps pipeline setups, enhance procedures, evaluate costs, and predict the timeframes required to complete a project by using data analysis and informative data.
5. Vulnerability scanning & Management
Before deploying code, all security flaws must be discovered and acknowledged. Ensure that a strict risk evaluation and all related examinations are in place well before the product enters the production stage.
Ensure that vulnerability scanners are performed well ahead of time, throughout the development and integration phases. Penetration testing and other possible attacks can help you with this.
DevOps safety runs a series of tests and techniques against the environment and infrastructure as product lines join the operational environment to confront patching problems.
DevOps safety can conduct tests on the production model to see if there are any problems. If they do, the team members can immediately begin working on updates or security fixes.
6. Effectively embrace the DevSecOps model right away!
Impactful DevOps security necessitates cross-functional cooperation and buy-in to ensure security factors are integrated throughout the product development phase, from product design and development to delivery, processes, and assistance, among other things.
DevSecOps will involve integrating administration and cybersecurity features, such as identity and access management (IAM), privilege monitoring, farewelling/unified threat administration, software testing, system integration, and vulnerability analysis all through the DevOps work process.
When done correctly, protection and DevOps are associated, allowing for efficient product updates while preventing costly recounts or repairs after code/products are launched.
To make this work, everyone must take responsibility for following security standards within their positions.
7. Deploy automated tools for ongoing protection
You might start utilizing security automation tools in DevOps processes to mitigate manual tasks for improved and continuous safety.
Introduce the automated processes into the picture so you can create repetitive tests against an application in addition to performing testing with the devices.
You will create safe products with ease using automated systems for code analysis, secret strategic planning, performance tuning, vulnerability analysis, and so on.
To wrap up!
With the widespread adoption of DevOps, security has become an increasingly important aspect of software development. With the accelerated future of software development and faster releases, you must strive for the end-to-end safety of your software distribution chain.
Securing DevOps paves the way for full-fledged DevOps execution. With security in place, DevOps is without a doubt a game-changing solution for developing business requirements.
When it comes to DevOps, there are many threats. So, to assist you, we have included some of the crucial DevOps security best practices that a company must follow to build secure applications and software.
If you are still unsure, you can hire a devops engineer for assistance.